DATA SECURITY
The CUMAN technology framework is SOC I and II compliant and is designed with the most rigorous data security standards that are continuously enhanced. Beyond CUMAN’s own data security standards, the framework is also protected through Microsoft Azure multi-level security framework.
CUMAN’S TECHNOLOGY FRAMEWORK
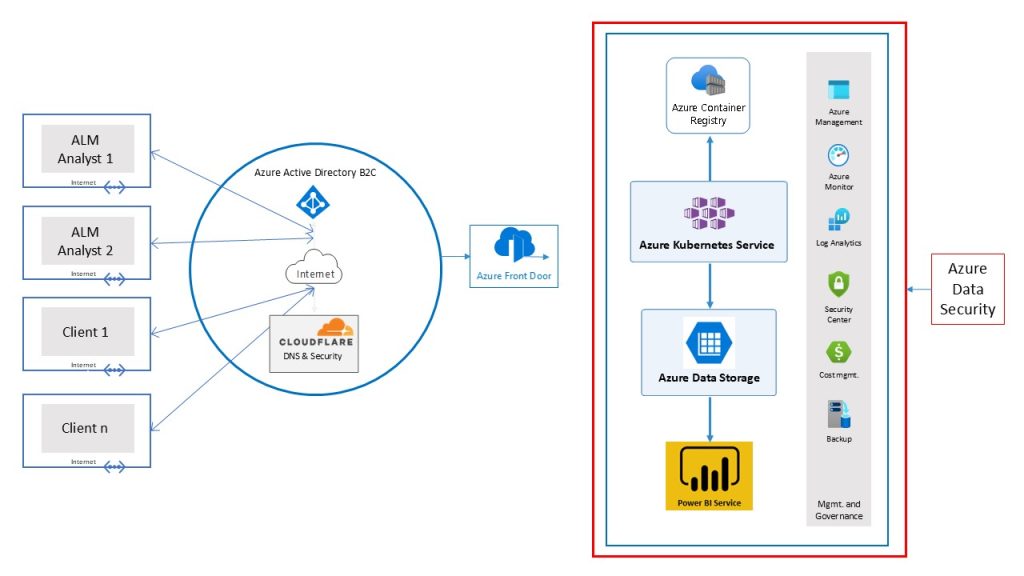
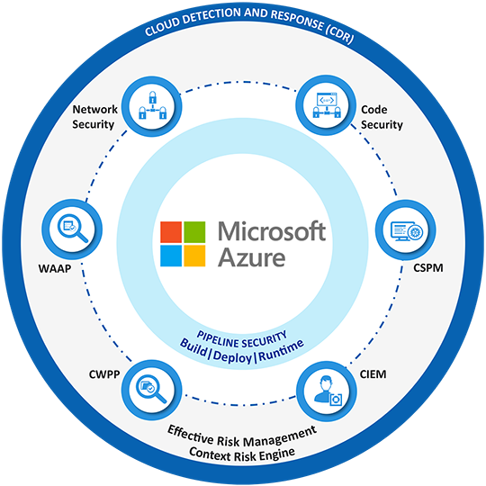
AZURE DATA SECURITY
- Key aspects of Azure Security
- Comprehensive Security
- Built-in Security Controls
- Azure Security Center
- Microsoft Sentinel
- Azure Firewall
- Azure Virtual Network Manager
- Microsoft Purview Information Protection
- Zero Trust Approach
- Cloud Adoption Framework for Azure Secure
Entra External ID
Microsoft Entra External ID is a powerful solution integrated into CUMAN to manage external identities securely:
- Authentication and CIAM: Entra External ID allows external identities to access apps and resources securely.
- Multi-Factor Authentication (MFA): Adds a layer of security to your applications by requiring users to provide a second method for verifying their identity during sign-up or sign-in. External tenants support Email one-time passcode methods for authentication as a second factor:
- Conditional Access: Policies that enforce access controls based on user, location, device, and application
- Identity Protection: Detects and responds to identity-based threats using machine learning
- Compliance: meets regulatory requirements with built-in security features
Azure Web Application Firewall
Azure Web Application Firewall (WAF) provides centralized protection of your web applications from common exploits and vulnerabilities. It is based on the Core Rule Set (CRS) from the Open Web Application Security Project (OWASP)
Default rule set (DRS) 2.1 is baselined off the Open Web Application Security Project (OWASP) Core Rule Set (CRS) 3.3.2 and includes additional proprietary protections rules developed by Microsoft Threat Intelligence team and updates to signatures to reduce false positives.
This security baseline applies guidance from the Microsoft cloud security benchmark version 1.0 to Azure Web Application Firewall.
Azure Kubernetes Service (AKS)
Azure Kubernetes Service (AKS) is a managed Kubernetes service used by CUMAN to simplifies deploying, managing, security, and scaling containerized applications using Kubernetes
- Security and Compliance: AKS is compliant with various industry standards and regulations, including SOC, ISO, PCI DSS, and HIPAA. It incorporates security features such as network policies, role-based access control (RBAC), and integration with Azure Active Directory.
Security of Azure Database
Azure Database for PostgreSQL flexible server encrypts data in two ways
- Data in transit: Azure Database for PostgreSQL flexible server encrypts in-transit data with Secure Sockets Layer and Transport Layer Security (SSL/TLS). Encryption is enforced by default. Uses SCRAM scram-sha-256 password_encryption, authentication.
- Data at rest: For storage encryption, Azure Database for PostgreSQL flexible server uses the FIPS 140-2 validated cryptographic module. Data is encrypted on disk, including backups and the temporary files created while queries are running. The service uses Galois/Counter Mode (GCM) mode with AES 256-bit cipher included in Azure storage encryption, and the keys are system managed. This is similar to other at-rest encryption technologies, like transparent data encryption in SQL Server or Oracle databases. Storage encryption is always on and can’t be disabled.

